Reputation
I define having reputation as having reputable third parties willing to confirm one’s claims as true.
These claims include:
- personal information such as one’s date of birth or first name,
- transaction information such as timely re-payment of debt following a credit card purchase,
- opinions expressed that are shared by others such as a blog post or
- actions done or not that are approved by others
- artifacts produced that are appreciated by others
Whuffie
Verifying someone’s claims used to be expensive and limited to a few players, such as credit bureaus in partnership with credit card networks. The recent computerization of communications has reduced the authentication cost by increasing the amount of authenticatable information (in the form of published opinion/thought pieces) and the potential number of authenticating parties, leading to my understanding of the concept of whuffie.
Linking with attention
I say “potential” because 3rd parties will not authenticate content unless one has their attention in the first place. Attention is limited the nature of people’s cognitive capabilities and is ideally dependent on their goals, but also a function of one’s reputation, which leads us to…
Social capital
The self-reinforcing aspect of reputation together with each person’s limited attention and exploding amount of authenticable information is what explains social capitalism: the authenticable information created by some is republished by others and through this process fully/partly appropriated because of their reputation. This is similar to Marx’ capital where part of the value-add of workers’ labour is appropriated by employers because of their ownership of the productive asset.
Examples include bloggers or journalists who are given exclusive information before it is published because of their established trademark. They don’t need anymore to find a good story, only to filter it out from what they receive.
Attention is the new capitalistic asset to own, maybe the new money considering that people’s attention is limited and that it is dispensable by those with social capital.
(Side note: assuming attention is driven by goals (see Flow), owning attention is done by getting others to align their goals on one’s goals).
Privacy
What is interesting about reputation is that it does not necessarily require information to be published. It only requires someone reputable to confirm it as true. I don’t need to tell you that I’m over 21 years old, but just need to point you to someone reputable that can confirm my claim.
In other words, privacy may not be dead, but it has to be dead with one or a few highly reputable parties.
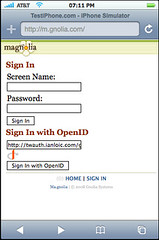
The relation to OpenId and OAuth
It derives from the above that an OpenId or OAuth provider’s relevancy is proportional to its reputation. Its value is proportional to its ability to actually verify the information it hosts.